Secret service agencies of the United States of America, such as NSA, have the ability to gather information about someone life. Edward Snowden, a former NSA employee, has leaked a lot of information about this. He exposed non secure mobile applications such as viber and angry birds, which transfer user`s data from mobile phones to secret agencies and companies. When a user is sending an email through some email applications, these connect for no reason to a proxy server before sending it. Why applications that are installed on mobile phones require so many permissions in order to operate since most of them are not needed by the application to function properly? How companies that provide 'free' applications are economically sustained? By ads or by selling personal data? Unfortunately, vast majority of mobile games and applications collect and sell or distribute users personal data (such as ip, user history and other data). This even happens by some VPN services that one pays for anonymity!!
Developers create Android applications usually with android studio. In it`s installation terms, you can see that Google as well as developers-companies gather data through applications they offer in playstore. Therefore whether ones personal data will remain actually personal depends on developers-companies.
NSA`s PRISM program gathers data from Microsoft, Yahoo, Google, Facebook, Paltalk, Youtube, Skype, AOL, Apple. With this program NSA can view and save these kinds of information about you: saved conversations, IM (instant messenger), to be notified when a user logs in or out to these services or sends messages, record VOIP conversations (voice over internet - e.g. Viber), even have access to photos, videos, activities, posts on walls even from companies that use open source software.
With Muscular program, NSA has access to Google`s cloud storage and users files, e-mail information, places someone has visited in Google maps, etc. Since December of 2020 Greek government is cooperating with Palantir company, which filters this enormous size of information that is gathered by all these systems and 'free' applications.
Google suggests that one should be logged in to use YouTube. While one is watching videos on YouTube, data about him are sent to servers belonging to various advertising and non-advertising companies.
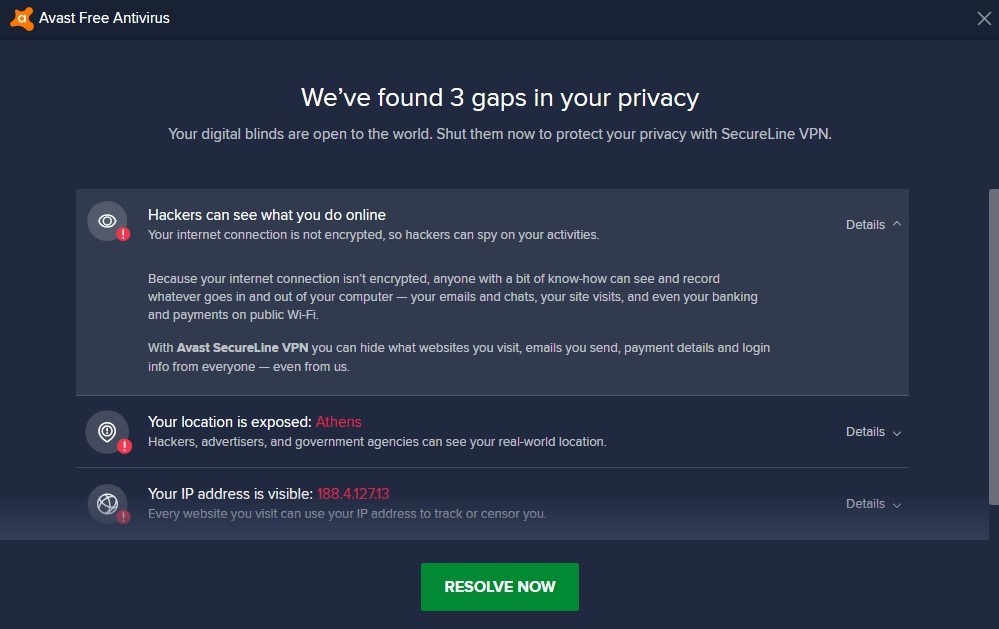
Avast antivirus warns that hackers can capture data that is transmitted to and from our computer and that our ip address and location are visible to them, our ISP, advertising companies and government.
Google nowadays is owned by USA military and therefore is an excellent NWO partner. It can record everything about someone`s life who is using their services. Check Google Dashboard. Check their policy. THEY COLLECT (PAY ATTENTION TO THE VERB THEY USE) EMAILS THAT YOU SEND AND RECEIVE, PHOTOS, VIDEOS, DOCUMENTS AND EVEN COMMENTS YOU MADE ON YOUTUBE!!! Google is not the only company that does this. Facebook, is characterized by Snowden as 'people tracking company' that sells user`s data for profit. From these data secret services can easily have access to an archive for each one it`s users that contains personal data, photos, videos, habits, psychological profile. Facebook recently has funded groups to remove posts they do not approve, by reporting them as fake.
Data can also be collected from the so-called smart devices that are also connected to the Internet (IOT), such as the Alexa Echo Plus. With it`s assistance, if someone is so bored to get up from the chair and turn on the lights he/she could ask from the machine to do it. One could ask it information we are usually looking for on the internet, it can play music, etc
21-05-24: With AI technology help (when AI will have access to personal data) that is being developed for the past 15 years or so, NWO will be able to predict if you are an enemy of them and perhaps what you are about to do next by using data that are described at list below along with phonecall data (look below this line).
It's really helpful for NSA that most data today globally (telephony and Internet) pass through US or it`s ally Great Britain through fiber optics which can be accessed. They have four programs for this purpose. These are: Blarney, Fairview, Oakstar and Stormbrew.
Cellphone communications can be recorded through equipment that has the ability to connect simultaneously to a number of lines at intervals specified by the service that uses this equipment.
Modern smartphones can be used as surveillance and audio recording devices through their camera and microphone, something that can not happen with typical cellphones, except some from Apple. Recording can also be possible if malware is installed to them. It can also be done through applications that have access to camera and microphone. Companies can activate them remotely so they can hear and see what is happening within a few meters of your mobile phone. This happens when these applications are enabled or open at background. On Android 6.0 and above, it is possible to disable microphone and camera use etc. for each application. Unfortunately, this is not true and applications have access to everything that is referred to their permission`s list, even if a user denies them to.
To understand how serious personal data and surveillance issue is, let us keep in mind that Mr. Levison of Lavabit, a provider of encrypted email services, was sued when he refused to hand over the keys that were used by his company to encrypt emails.
Unfortunately, there is a foolish general opinion about privacy: since you are not doing something illegal, why do you care? Imagine that you are at one of your favorite places and you watch something on your cellphone or you write something down in a book. A stranger comes behind your back and looks at what you are doing. Do you feel nice? Will you say to him: keep watching?
It is our right to protect our personal data and anonymity on the internet. So one should:
Use software and services that provides anonymity and protects personal data.
Configure Windows 10 so they make as less as possible connections to data collecting servers.
Disable personal data collection from Google.
Delete Gmail from Google account if you don`t want other people to see your e-mail as well.
Disable Google`s services and applications from Αndroid based smartphones.
Replace Google`s Android from smartphone with another Android-Linux based OS.
 |
 |
 |
 |
 |